We use a web based documentation system at work and have had a couple of instances where data for companies (ie Company X) seems to have been randomly edited in forms to include data from another form (ie Company Y) in the system. In a form that had a username, password, url and notes field we discovered that a tech could go in and edit the notes (and only the notes field) and without realising it, the username and password were also being updated in the form. The tech would hit save and now the saved password was incorrect.
Thankfully the documentation system has revision histories to allow us to revert back to the previous settings. but it is still a painful process to go back and review recent changes to see which ones were genuine edits and which were changed incorrectly.
We initially blamed it on LastPass filling out data as the issue would not occur if we disabled LastPass, however a search in LastPass would not return the data that was being added to the form. It took us a while to track down, but Chris, one of our techs worked out what was going on.
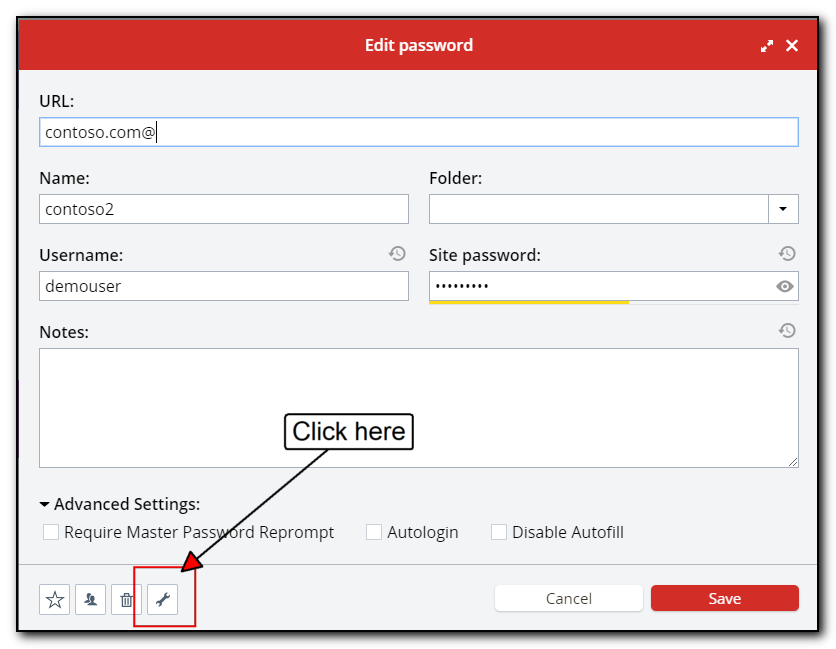
LastPass has additional fields that don’t show up when you browse (and apparently search) and the data from these extra fields were automatically being filled in for some reason. Click the wrench, highlighted in the above screenshot to see the extra hidden fields.
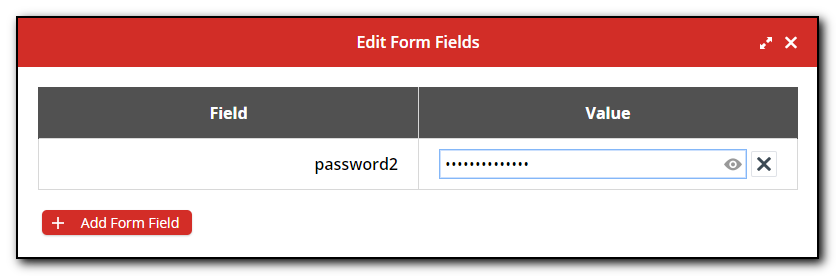
Our solution was to delete these extra fields, save the record in LastPass and we no longer have LastPass corrupting our data.

 One of my annoyances with Office365 administration tasks was that I could make changes to the interface but had no idea what commands were being run behind the scenes. This made creating scripts a frustrating trial and error attempt at finding the correct verbs to run.
One of my annoyances with Office365 administration tasks was that I could make changes to the interface but had no idea what commands were being run behind the scenes. This made creating scripts a frustrating trial and error attempt at finding the correct verbs to run. We’ve been tracking down issues with Windows Server 2016 on a multitude of servers this week where the servers will reboot and come back with Unmountable Boot Volume which is a pretty nasty experience for oncall. So far we’ve mainly seen it on Domain Controllers but also on a Hyper-V server. The solution is typically to do a last known good boot on the machine and then try to work out what has changed on the server and needs redoing. So far we’ve had issues with duplicate servers in Webroot and Automate along with a couple of server functions not working correctly.
We’ve been tracking down issues with Windows Server 2016 on a multitude of servers this week where the servers will reboot and come back with Unmountable Boot Volume which is a pretty nasty experience for oncall. So far we’ve mainly seen it on Domain Controllers but also on a Hyper-V server. The solution is typically to do a last known good boot on the machine and then try to work out what has changed on the server and needs redoing. So far we’ve had issues with duplicate servers in Webroot and Automate along with a couple of server functions not working correctly.