TLDR – set the api key whilst having a meeting with yourself
I was fortunate to get a Streamdeck for a birthday present back in March this year – the announcement that it was integrated into Teams was the final push to get one. I had been debating whether to get one or not and had been using TouchPortal as a software solution running on an old Kindle as test bed for quite some time to see how much I would use this functionality. The answer is a lot!
(Very) Shortly after getting the device and setting it up, the Teams plugin was pulled from the store but eventually re-released and it has never worked since. If I was lucky it would intermittently work for 5 minutes or even 20 if there was a blue moon, I was wearing my lucky jumper and there was a z in the day’s name.
Other people have also had the same problem and there has been a long thread on the elgato subreddit about the issue with various solutions provided but none of them have worked for me, at least on a consistent basis.
However a post yesterday on the Microsoft community forums had someone getting the plugin working with the new Teams version. I followed the steps and the issue was still not working for me – however it did give me a clue.
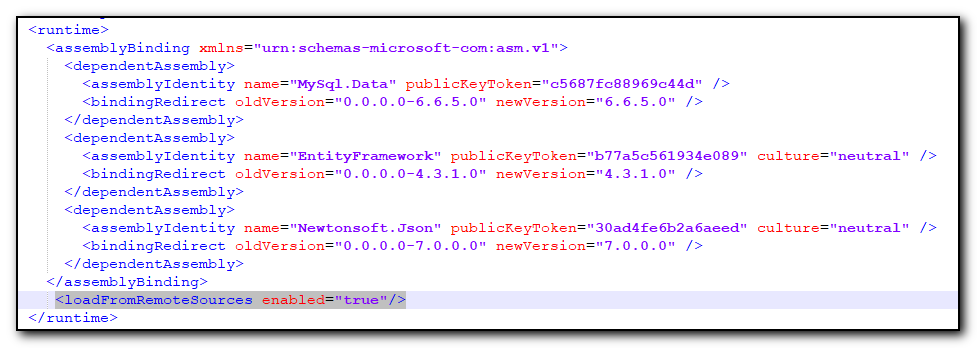
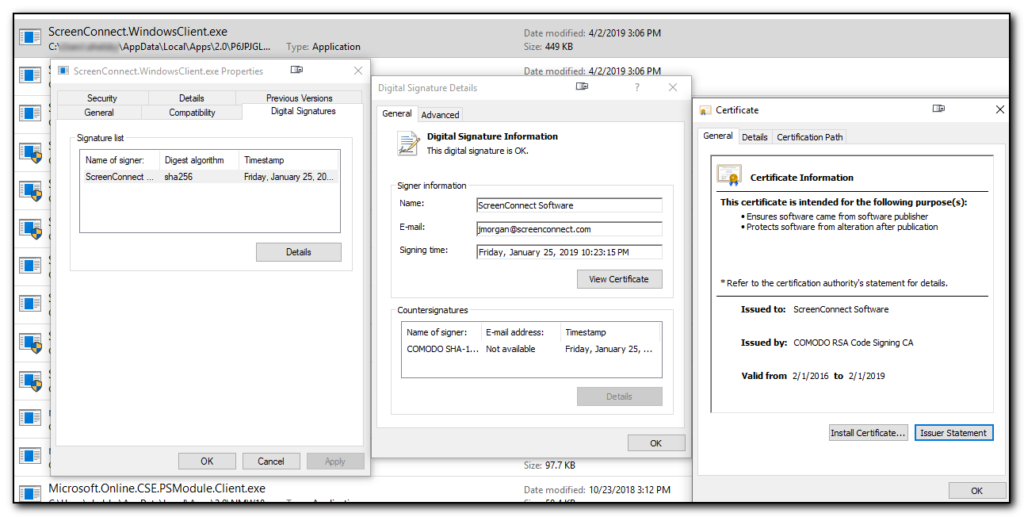
This morning I confirmed that the WebSocket was listening on port 8124 with netstat -aon | find “8124” and was fiddling around trying to get the plugin to work. I had already confirmed the api key (found from Settings/Privacy in Teams and pasted it into the plugin settings and was still getting the lock icons, but this morning I selected the calendar, “Meet now” option and started a meeting with myself. (It was very early and there was no one else to call!)
After the meeting was established, I opened the plugin and re-entered the api key in the button settings and this time the setting worked, all of my buttons had the padlock overlay removed.
Fearing the worst, I killed the meeting, restarted Teams and Stream Deck, and all the buttons are still working. Being the optimist, I then rebooted the computer, restarted Teams and Stream Deck and the buttons still work. 2 hours later and the buttons are *still* working.
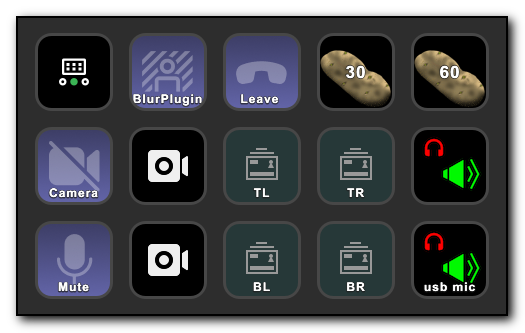
For those interested, the TL, TR, BL, BR refer to the monitors attached to the desktop computer and enable me to quickly switch the OBS camera to the relevant monitor. Using the classic Teams app allows me to share a video feed from a camera so all I have to do is share the one video stream and let OBS and Streamdeck take care of everything else. Unfortunately, the New Teams does not have this functionality and the OBS output screen needs to be shared which requires way more key presses to setup and the OBS output running on one of the monitors, so until this shows up in the New Teams application, it’s Teams Classic for me.

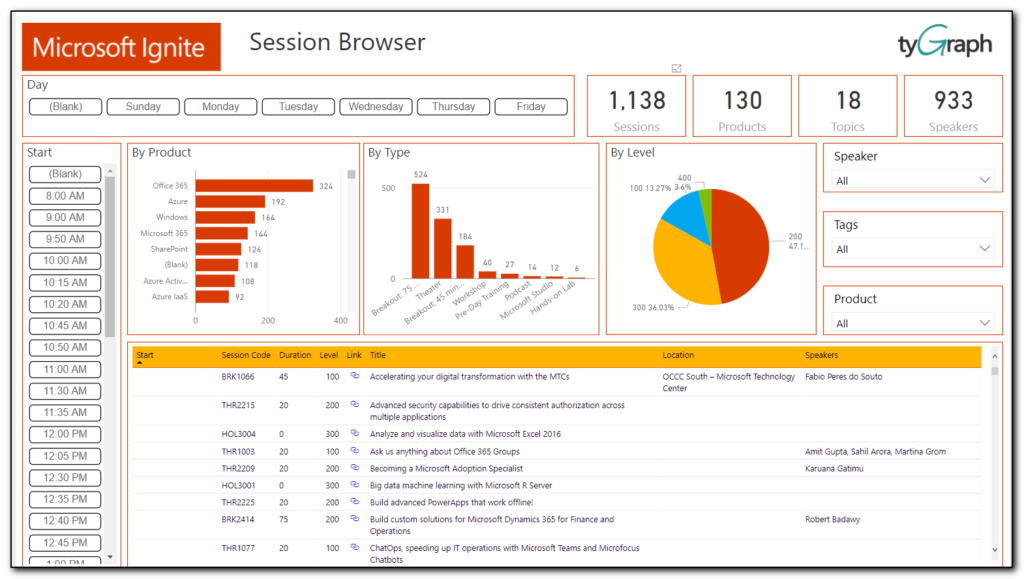
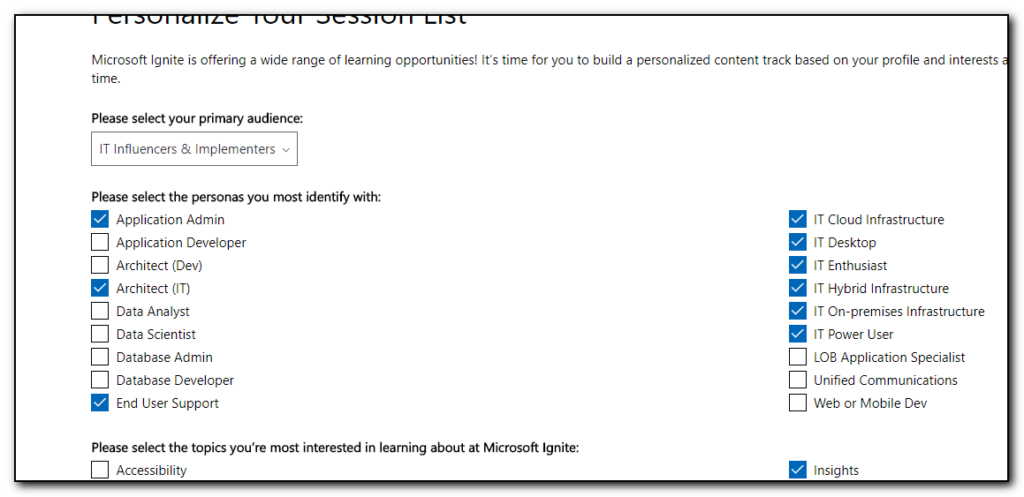
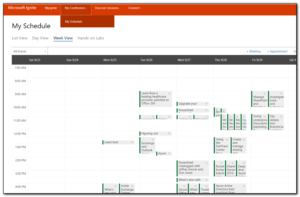
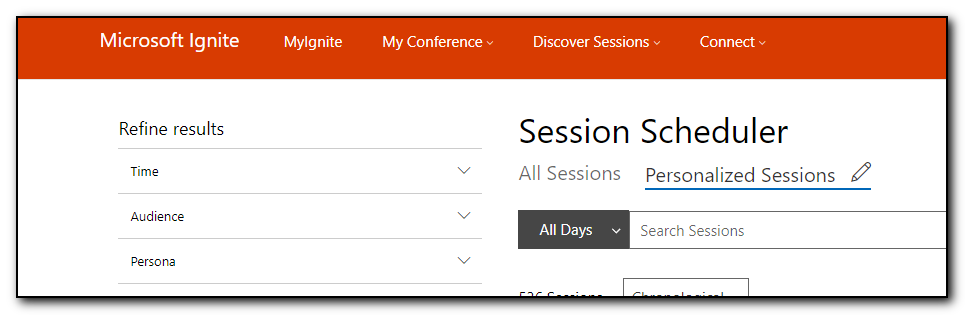 I then went through this list and selected the option to add to schedule option to select all the sessions I am interested in. Some of these sessions are ones that I would want to download and view later, some of them are ones that I want to attend. Right now I do not see a way of prioritizing these sessions as must attend, 1st choice, stream later – hopefully this is possible in the future.
I then went through this list and selected the option to add to schedule option to select all the sessions I am interested in. Some of these sessions are ones that I would want to download and view later, some of them are ones that I want to attend. Right now I do not see a way of prioritizing these sessions as must attend, 1st choice, stream later – hopefully this is possible in the future.