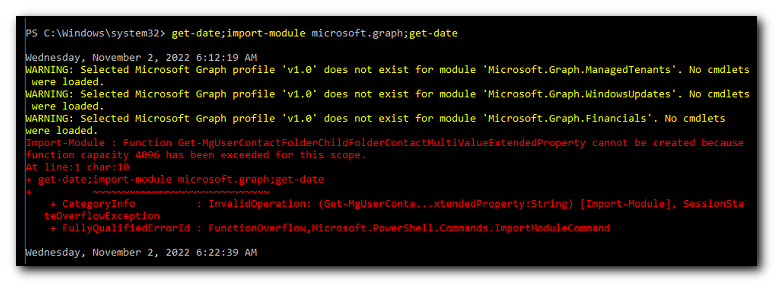
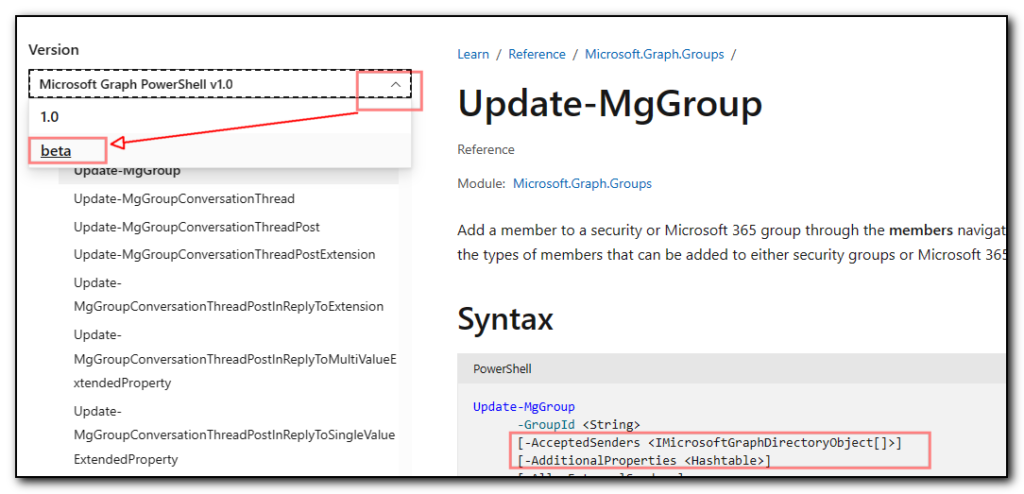
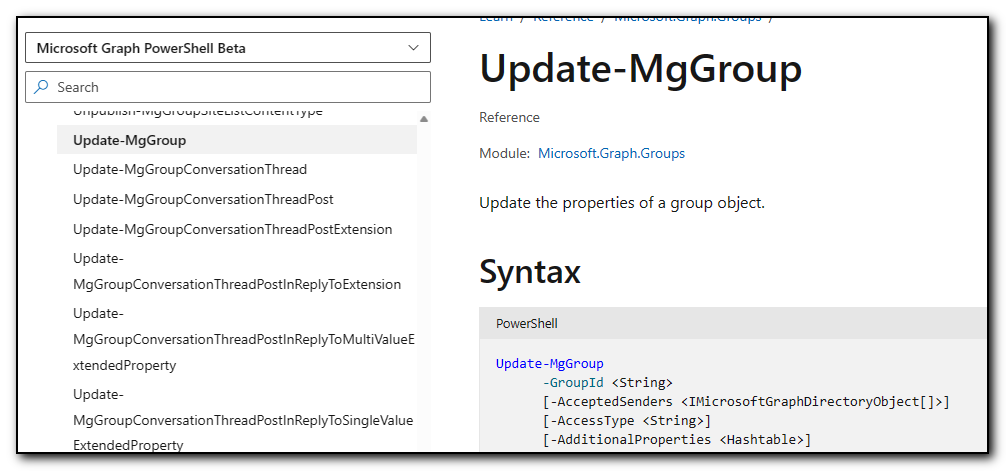
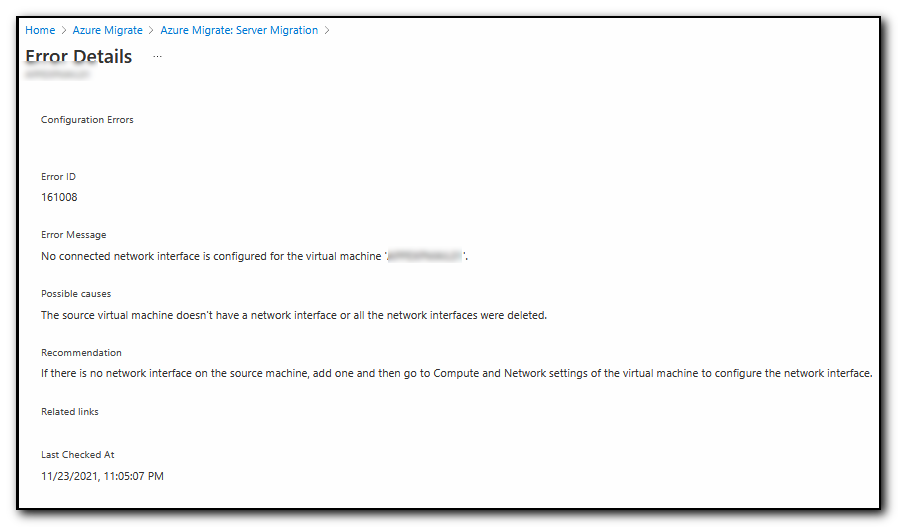
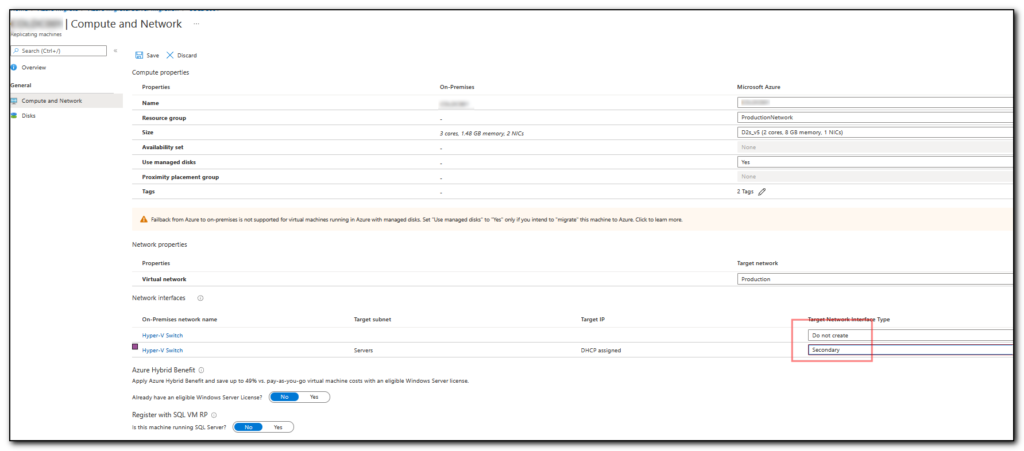
Check application log and probably will see event 8193 “Failed to create restore point”.
In our case, this was because the system restore point was disabled/ set to 0 bytes.
This can be checked with
vssadmin list shadowstorage | findstr /B “No items found that satisfy the query”
and fixed with
vssadmin resize shadowstorage /on=C: /for=C: /maxsize=30GB