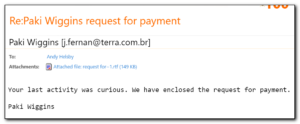
I just signed up for my first Kickstarter project for the remotsy package. A device that integrates with smartthings and alexa to control your remotes by voice. No more moving the cat and dog to see if they are sitting on the remote or hunting for them if they are not underneath them – instead I can just say “Alexa – continue watching Gilmore Girls” and the bluray will turn on, along with the tv and the lights can dim. This will be useful to reduce the number of remotes for our home entertainment system(currently at 4 total).
Watching the demo videa was amusing as they demonstrated Alexa commands – naturally my Alexa heard the ad and chimed in and although it got the time right, everything else was a “Sorry I don’t understand”
At $57 including shipping for a beta and a retail device it’s also pretty reasonably priced. There are quite a few packages left at the moment, but the project has just been released so I expect it to sell out pretty quickly