It was an interesting week at work with several malware infections making it through the various av protections that we have in place which proves that end user education should be your primary line of defense in the fight against virus’. It is amazing how often people will click on random emails that have been sent to them with random filenames just because the email arrived in their inbox (or in another mailbox that they happen to have access to), even if it was not addressed to them.
I was lucky enough to get one of these emails through to my corporate mailbox on Tuesday this week, evading detection by McAfee email protection and Forefront on the desktop. (Using another av solution would not have prevented this as you will see later)
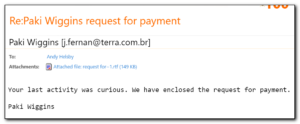
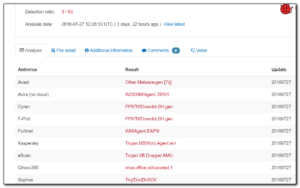
This was obviously some scam with the description of the user not even matching the email address of the user. Being curious, I naturally saved the file to my hard drive and then uploaded it to virustotal. On Tuesday, only 1 of 58 av engines recognised this as a virus – kudos goes to Quihoo-360 for being the sole detector. I must admit that I’ve never even heard of this software and I was very surprised to see that only 1 av vendor recognised the file.
I submitted the file to McAfee for scanning by zipping the file up with 7-zip and password protecting it with the phrase infected and sending it to their response team at [email protected]. Incidentally, McAfee’s instructions for doing this are very outdated as Windows10 no longer has the option to password protect a zip file. McAfee immediately came back saying that their analysis was inconclusive and the file had been submitted for further research. This was an improvement on the previous sample I had submitted on Friday for a cryptolocker variant that came back as no virus found!
Wednesday morning I uploaded the file to virustotal again to see what the state of detection was.
This time the detection rate was slightly better – 9 products including Sophos that I use at home, but neither of the products in use at the office.
Thursday morning, two days after receiving the virus I received a response back from McAfee that confirmed the file was malicious. They included an extra.dat that would detect the file.
By this time, virustotal was showing 25 out of 53 products detecting the virus so it is getting better. Microsoft’s product was listed as detecting the file, yet Forefront was still passing it through as clean. Although virustotal has the definition date of 7/28, my computer was showing “defs of 7/26, update on 7/27”. Not sure why there is this discrepancy of the definition dates.
Yesterday, my laptop at home still had old definitions as it was not connected to the corporate lan and was still showing the file as clean which is pretty scary.
This morning I downloaded the file to my personal laptop, saving the file with a .txt extension so I would not accidentally open it – something that is easier to do on a touch screen tablet. Interestingly Sophos did not detect anything wrong with the file. Launching the file in notepad, it starts with the letters PK which implies the file is actually a zip file and there are several strings referring to HP printers and Adobe Photoshop.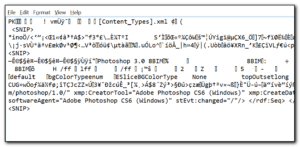
At this point I’m not going to risk my machine further by opening it with 7zip to see what happens.
However when I copied the file to .zip or to .rtf Sophos did spring into action and quarantine the file. This is really handy as it protects the file from being saved to the machine in an executable form, but also allows you to save the file to the hard drive for further analysis in your debugger of choice. Other applications will quarantine the file no matter what the extension is, making it harder to retrieve. On the other hand, you now have an infected file on the machine that av is not discovering.
This Sunday morning, I uploaded the file to virustotal again. This time we’re slightly better at 29/54 detections. However, Comodo, Malwarebytes, Panda, SuperAntiSpyware,Symantec, TrendMicro and Vipre (among others) do not detect the file as malicious.
Malware bytes is an interesting discovery as it’s not usually regarded as an av product as it typically protects you from software being installed into suspicious locations such as autorun, startup, browser toolbars etc as opposed to traditional av that scans every file being written or read to the hard drive. However in this case and my recent cryptolocker, MalwareBytes failed to find anything malicious although HitManPro did find the Cryptolocker exe file on the machine (but MalwareBytes and McAfee did not).
The best av is the human kind that recognises a file is suspicious or unexpected and does not open it – although even this kind of av can fail (and some are more prone than others!)
Incidentally, one of my favourite solutions for the Cryptolocker variant, in theory at least, is pretty drastic and requires the permissions of file shares to be changed so that files can be created but they can’t be edited. Users (and software) would be able to write new files to the file share, but any edits to the file would not be allowed unless the changes are written to a new file. This forces users to do Save-As all the time, may break Office documents that insist on modifying the original file, but would stop Cryptolocker from overwriting files on the drive. Obviously this takes up a lot more disk space and would not be suitable for shares holding Autocad documents.
*Please note that this post is not meant to denigrate any one particular av product in particular as I understand that definitions take time to produce but av software that does not detect infections 5 days later should probably be evaluated to see if it is safe for continued use. I do reserve the right to moderate comments on this post if they are not helpful and just say “Product XYZ is useless”