-
SCRIPT: InternalExternalURLs.ps1 « msunified.net
Awesome powershell script for configuring/checking Exchange 2010 autoconfiguration urls for internal and external access. Far easier than tracking down the obscure powershell commands.
Apparently Linkedin now have a feature that allows users to provide their corporate passwords to a third party so the users can then send invites to other people in their office. I really don’t see how this can Be A Good Thing 😉 – Paul Cunningham has a post on ExchangeServerPro on this feature and links to Adam Fowler’s post on how to block LinkedIn to Exchange. This is interesting as we’ve also seen this issue with Verizon doing something that we expect is screenscraping to provide email information to phones. Admittedly this was a while back but we have found it hitting the Exchange server so it will be interesting to see if this successfully blocks the server.
In a meantime, maybe it’s time to not only educate LinkedIn that this is a really bad idea but also your corporate users.
For what it’s worth the solution is to do the following:-
There are a few settings to check. First, under the Set-OrganizationConfig area, you’ll need to check that EwsApplicationAccessPolicy is set to ‘EnforceBlockList’. If it’s not, it’s going to be “EnforceAllowList” and you’re probably OK, as it’s using a whitelist for access to only what’s listed rather than a blacklist, to only block what’s listed.
Next, you need to add LinkedIn into the BlockList. This is done with the command “Set-OrganizationConfig -EwsBlockList LinkedInEWS“
This morning I was working on a Sites and Services issue for a client and part of the troubleshooting process was to run the Best Practice Analyzer on the domain controller. One of the results was to enable client fallback to the local netlogon and sysvol share after the local domain controller comes back online again. This reduces traffic across the network. I’m not quite sure why this is not enabled by default.
The BPA points to the technet article DFS-N: Client failback should be enabled for the Netlogon and SYSVOL folders on domain controllers. Scrolling through the page I was pleasantly surprised to see my avatar at the bottom with a comment on improving the documentation with the actual registry keys that needed changing. Not only was my comment on the page, the original web page had been updated to include the information.
It’s nice to see content updated based on user feedback. It’s not nice to see that I had this problem 3 years ago 😉
-
Integrating DaRT 8.0 SP1 Remote Connection into the SCCM 2012 OSD Process | Anything about IT
-
Microsoft Anti-Virus Exclusion List – TechNet Articles – United States (English) – TechNet Wiki
-
More time work – note the change in April on time settings for the DC
Last week my mobile phone started to constantly download a Facebook update which was draining the battery due to the constant downloading attempts. Trying to stop the download, I somehow managed to disable the download manager – this did fix the problem but for some reason also stops the Google play store from working. Every time I opened Google Play the application would just disappear from the screen. There was no forced close error message. This was a bit of a problem as I had removed the Facebook app from my phone trying to stop the download and then was unable to reinstall it as the store would not open.
To fix this issue, Open Settings, Application Manager, scroll to All applications and then scroll down to the bottom of the screen. It is necessary to scroll all the way down as the disabled applications are at the bottom of the alphabetical list. Click on Downloads and then enable the application.
The app store will then start working and hopefully you won’t get the facebook update pushed down to your phone (I didn’t at least)
-
Enabling or disabling single sign on.
I have been battling this install for 2 days so far and not getting anywhere. There are a ton of sql prerequisites and the install error messages are very vague, like this message below:-
Surely it can’t be that hard to display the version of SQL server that is detected.
I’m currently following Harold Wong’s System Center install guide along with Matthew Peter’s guide and downloaded the Cumulative update 10 for SQL.
Attempting to install this patch on the server gives the error message below.
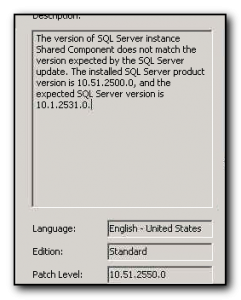
The stupid thing about this is that neither 10.51.2500.0 or 10.1.2531.0 are valid sql version numbers. Select @@version returns the accurate 10.50.2500.0 which is sql 2008 r2 sp1 but it ignores the previous cumalative update that I’ve already installed.
So far my hopes for System Center have been severely dashed and buried in the ground. It’s a good job we don’t have windows in this office or I’d be tempted to set fire to the server and chuck them out of the window.
It’s been a long start to the new year.
