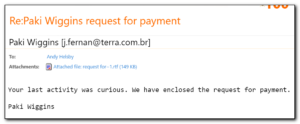
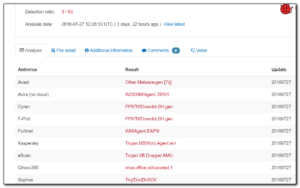
Filing for future reference for reference in case of a ransomware infection. This list gathers together a list of tools and references that may allow you to get access back to encrypted files.
- Kasperky’s Decrypters
- Kaspersky’s AntiRansomware or Cryptoprevent– prevent infection in the first place
- Avast Decrypters (Multiple tools available)
- Trend Micro Decrypters – Multiple decrypters available
Remember the best way to not get infected is to install a cryptolocker prevention tool (I use the Cryptoprevent), watch the sites you go to, educate yourself on what a phishing attack looks like, don’t run as administrator, use opendns (or google safe browsing) and ensure you have a good backup that is not accessible from your normal machine with your normal credentials.
If you know of any others then please let me know.
Edit – https://www.nomoreransom.org/ is also a good resource and probably should be your starting point. It even allows you to upload an encrypted file (or the ransom note) and will then check what version of crypto you have and let you know if there is a decrypter available for you.