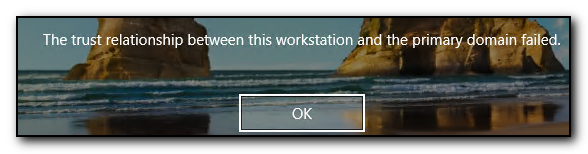
Yes, this old chestnut! Had this issue today on a server, but for some reason the standard netdom resetpwd command would not work.
Running the command netdom resetpwd /s:servername /ud:domain\user /pd:* would give me the error message “The machine account password for the local machine could not be reset”
Powershell to the rescue and the equivalent commands running on the affected machine fixed the issue
$c=get-credential
test-computersecurechannel -repair -credential $c
shutdown /f /r /t 3
Unfortunately I’ve had to this multiple times in the past and it’s about time I blogged the solution for my own reference in the future